IAM Challenges
- User Password Fatigue
- Failure-Prone Manual Provisioning & De-Provisioning Process
- Compliance Visibility: Who Has Access to What?
- Siloed User Directories for Each Application
- Managing Access across an Explosion of Browsers and Devices
- Keeping Application Integrations Up to Date
- Different Administration Models for Different Applications
- Sub-Optimal Utilization, and Lack of Insight into Best Practices
How do companies currently manage their user identities?
- IT-Managed Lifecycle Management
- HR-Managed Lifecycle Management





Universal Directory
UD has following profiles:
- Okta User Profiles
- Every kind of account, no matter how they are mastered, has an Okta user profile.
- The base Okta user profile has about 31 attributes by default which cannot be removed, but can add as many custom attributes.
- Directory Profiles
- If your accounts are mastered by AD, we can map the AD profile attributes to the Okta user profile attributes as needed.
- Schema Discovery to get AD attributes to Okta.
- When you set up an integration with AD, you see that Okta has pre-selected several of the most common attributes in AD to bring into Okta. This is done when setting up the directory user profile during Step 3 of the Active Directory integration process.
- Supports custom attribute as well.
- Application Profiles
- Box has 4 attributes in its user profile.
- Google has over 200 attributes in its user profile.
- Salesforce, which has a custom schema, can have all different kinds of attributes.
- So these application user profiles can really look drastically different than say the Okta user profile because the information they need will vary depending upon the application.
- Application User Profiles that are UD Enabled will have the ability to perform schema discovery, enabling Okta to read the attributes in the application profile and connect them to Okta.
- Identity Providers Profiles
- There may be profiles you see for IdPs such as in a Business to Consumer (B2C) scenario where we want to let our users login with an application like Facebook.
- Facebook can become the IdP thru the notion of social authentication.
- Okta becomes the Service Provider, offering an enterprise grade solution around this scenario.
Profile Mappings, Profile Masters, Profile Editor
- Profile Mappings -> Mapping between source and target and vice-versa.
- Schema Discovery discovers attribute-metadata from source or target apps.
- Expression language useful to transform the attribute in and out of Okta.
- Profile Editor -> Helps to add/ edit/ delete custom attributes and edit regular attributes.
- Profile Masters -> Tells which is a user source of truth for user profile attributes in Okta. eg: Okta, Directory or App.
- Currently, if more than one profile master exists on the Profile Masters page, they can be prioritized so that end users can be mastered by different systems, based on their assignments.
- At any given time, there can only be one profile master that masters a user’s entire profile.
- A user can only be mastered by a single application or directory at any one time.
Profile mappings allow administrators to precisely control the attributes exchanged during provisioning processes. The two chief use-cases that UD facilitates are:
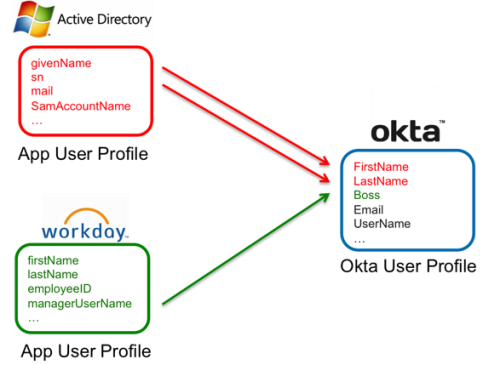
App to Okta
- In this use-case, organizations typically use a source-of-truth app such as a directory or HRMS.
- Some organizations might have several sources of truth.
- Mappings define how attributes from these various sources are imported into the Okta user profile.
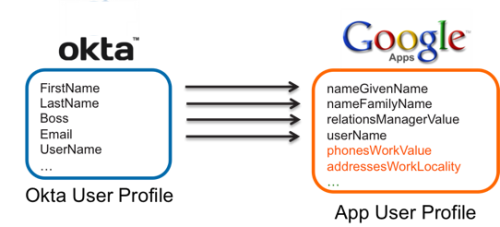
Okta to App
- In this use-case, organizations want to propagate the data in Okta to other applications to provision accounts and update accounts with rich data.
- This is possible if the Okta user profile has rich attributes and the app in Okta is UD-upgraded.
- Attribute Level Mastering (ALM) delivers finer-grain control over how profiles are mastered by letting you specify different profile masters for individual attributes.
- Without it, all of a user’s attributes are mastered by a single profile master.
- Setting up ALM:
- Enable Profile Mastering
- Prioritized profile masters on the Profile Masters page

- From the Directory drop-down menu, select Profile Editor.
- From the Master priority drop-down list, select one of the following:
- Inherit from profile master: Picks up the default profile master for the entire profile, as shown in the Profile master priority field.
- Inherit from Okta: Picks up this particular attribute value from Okta. This attribute value can be edited in three ways: via the user’s Profile tab, the Okta API or, if appropriate for end-user modification, by the end user.
- Override profile master: Overrides the default profile master. Click the Add Master drop-down menu to choose another available profile master. Note that this option does not generally disable the app as a master.

- From the Master priority drop-down list, select one of the following:
- Desired mappings are specified through UD mapping
- The optional third step of setting up ALM is to map the attribute through UD. If you changed an attribute’s Master priority to Override profile master, for example, the attribute now has a null value and must be mapped. To map the attribute, do the following:

| Example Profile Master Set | |
| Profile master: Default master for the entire profile. |
Workday, Active Directory |
| Attribute master: Alternative master for a particular attribute. | 3rd attribute: mobile phone = Active Directory
All other attributes: Workday |
| Example Attributes | |
| First name | Workday |
| Last name | Workday |
| Mobile phone | Active Directory |
| Work phone | Workday |
- App (master) <-> Okta <-> App or Okta (master) <-> App <-> Okta
- Enabling Profile Master and Update User Attributes for the same application allows to push Okta to App profile mappings to your highest priority profile master.
- This is beneficial when you want to sync attributes from downstream applications back to the profile master, like an email address and phone number from an app back to the master Workday profile.
- However, you may lose data if an app that you designate as profile master can also receive profile updates from Okta.
- Caution: Enabling both Profile Master and Update User Attributes for the same app may result in:
- Unwanted profile pushes – Okta updates can overwrite the values of unmapped attributes in an app, even if that app is the highest priority profile master. For example, if the cn attribute is not mapped from Active Directory to Okta, and you’ve configured Active Directory for Profile Master and Update User Attributes, Okta will apply a default mapping to cn.
- Overwritten IdP-mastered attributes – Okta to App updates can overwrite attributes that are mastered by another identity source. There’s no partial push option.
- Race conditions – Okta can overwrite an updated attribute in an identity source before other updates are pushed back to Okta.
- For example, consider a scenario in which a user’s first name and last name are imported into Okta from a directory, but the user’s email address is imported into Okta from an app. If the user’s last name changes in the directory before the applicable email address update is made in the app, Okta could push the new name and the old email address to App.
Username Overrides
- Username override can also be used with Selective Attribute Push to continuously update app user names as user profile information changes.
- For example, if a user gets assigned to an app with a username of email, and that email subsequently changes, Okta can automatically update the app username to the new email.
- Prior to this enhancement, an Okta admin had to manually change a user’s app username by unassigning the user and reassigning him to the app.
- This enhancement applies to all apps and is not limited to only apps with provisioning capabilities.
Overriding the App username
- For the Okta to App flow, you can no longer override username mappings in Profile Editor.

- The username mapping displayed in the app’s Sign On tab will be the source of truth for the Okta To App flow.
- Updating the username mapping on Create only or Create and Update will also be managed from the app’s Sign On tab.

Overriding an Okta username

Exclude username updates during provisioning

People
There are 3 types of people or user accounts that can exist within Okta:
- Okta-Mastered people
- Directory-Mastered people
- Application-Mastered people
- Okta-Mastered People can only be added to Okta groups (groups created in Okta), as opposed to groups that have been imported from an external directory service such as Active Directory Groups or LDAP groups.
-
- Login via Okta Password policy and they are governed by the Okta User Profile, which is to say that the primary source of truth for the user’s attributes is the Okta User Profile.
- Any active user can be assigned an Okta Administrator role (both Okta-Mastered and Directory-Mastered people, are eligible for admin role assignment).
- Okta Super Admin and Org-Admin are in charge of managing the password policy for Okta-Mastered accounts.
- When importing people records via the CSV template, you cannot import more than 10k records per file, and the file size cannot exceed more than 10MB.
- As a best practice, you will need to create at least two Okta Admin Service Accounts and assign Super Admin rights to the accounts.
- Directory-Mastered people log into Okta using the same credentials they would use to log into their on-premise workstation.
-
- Directory-Mastered people are governed by the Directory user profile—management of user attributes must be done in the directory service.
- By default, Directory-Mastered people cannot change their directory-linked password within Okta.
- However, an Okta Super Administrator can configure the Directory Password policy in Okta to enable this ability.
- Directory-Mastered people can be associated with both Okta groups and Directory groups.
- AD app user profile schema requires both the first and last name.
- You can create an Okta mastered user without a first or last name, but you cannot import an AD user into Okta without a first and last name.
- Delegated authentication and Just-in-Time provisioning will automatically be enabled as part of your AD/ LDAP installations.
- System Requirements
- Windows server must be running Windows Server 2008 R2 or newer and have at least 256 MB of RAM available.
- The host server of the agent must also be a member of the same domain as the Active Directory users.
- The Windows server where the agent resides must be on at all times. In other words, don’t install it on your own desktop or laptop. The agent host server must have a continuous connection to the internet so it can communicate with Okta.
- Best practice: ensure high availability and provide a failover if need be, you should install at least 2 Okta Active Directory agents on two different servers connected by any one domain.
- That is to say 2 agents for every domain. You can either install the Okta Active Directory agent on domain controller and/or any two active servers connected to domains.
- OUs
- Organize people and groups into AD OUs.
- Okta will only import users accounts and groups within OUs.
- User Accounts for AD agent
- A local AD domain administrator account to run the Active Directory agent installer; this is only required for the installation.
- An Okta Super Admin account.
- An Okta-AD service account which is created via the integration wizard and becomes a service account that the service runs after installation.
- This account serves as the liaison between AD and Okta, and by default has read only access to AD.
- It is the AD Agent that will pull information from AD into Okta and keep that information synchronized.
- User Accounts for LDAP agent
- A local LDAP service account which will be created during the installation process of the LDAP agent.
- An Okta administrator account which will be used to connect Okta to the LDAP agent.
- A LDAP user which must have the ability to look up users and groups or roles within the Directory Information Tree.
-

JIT
- JIT account creation and activation only works for end users not already Okta.
- JIT updates the accounts of existing end users during full imports.
-
- This means that end users who are confirmed on the import results page, regardless activated or not-activated are not eligible for JIT activation.
- When JIT is enabled, users do not receive activation emails.
- If delegated authentication is enabled, NO need to import users from AD first for JIT provisioning to create Okta accounts.
- If NO delegated authentication enabled, MUST import the AD accounts first, and they must appear on the imported users list for JIT provisioning to create Okta accounts.
- JIT automatically:
- Confirms and activates the account.
- Updates any attributes for accounts already activated, when the person next logs into Okta.
Schedule import allows how often you want to run scheduled imports of people records from Active Directory into Okta.
- With each import:
- Any user attributes that may have changed in AD will be updated.
- Any new user accounts created in AD since last import will be imported.
- Always manually initiate the importing process from the Import tab.
- Matching the imported users:
- Exact match:
- username
- attribute (base or custom)
- attribute combination
- Partial match:
- Partial matching of:
- firstName
- lastName
- No match of:
- username and/or
- Partial matching of:
- Exact match:
- Confirm the imported users:
- Confirm matched users: Select to automate the confirmation or activation of existing users.
- Unchecked, matches are confirmed manually.
- Confirm new users: Select to automate the confirmation or activation of a newly imported user.
- If this option is selected, you can uncheck it during import confirmation.
- Note that this feature does not apply for users who already exist in Okta.
- If activated JIT, no need to confirm or activate the users. Users are activated during signin.
- Confirm matched users: Select to automate the confirmation or activation of existing users.
Profile & Lifecycle Mastering
App to profile master Okta users.
Once enabled, the app appears in the list of profile masters on the Profile Masters page.
- Allow <app> to master Okta users: Determine what happens when a user is deactivated or reactivated in an app.
- Only the highest priority profile master can deactivate or suspend an Okta user.
- When a user is deactivated in the app: Choose to:
- Deactivate
- Suspend
- Do nothing:
- App controls user cycle but allows profile master of attributes and mappings.
- When a user is reactivated in the app: Choose whether reactivation in the app applies to suspended or deactivated Okta users.
- Reactivated in the app, the user profile must be an exact match to the Okta profile.
- Otherwise, after importing the reactivated users, they appear in Pending Activation state.
Clearing unconfirmed users
Allows admins to clear all unconfirmed users within an import queue.
- Impossible to select and remove specific users at this time.
- The only option is to clear all users.
- If an admin mistakenly clears all users from the queue, they can rerun a full import to restore the queue back to its prior state.
- To restore the import queue, an incremental import will not suffice—a full import is required.
- Also note that, if an existing (scheduled or manual) import is actively running, admins cannot clear users. The Clear Unconfirmed Users button is unavailable until that previous import is complete.
- If a scheduled or manual import is started during a clearing process, it is queued up to begin as soon as the previous operation completes.


Import Users from App
Directory

- Directory Integration for All Cloud Apps
- UD is made available to all Cloud Apps
- For AD integration, Okta provides three lightweight and secure onpremises components:
- Okta Active Directory Agent: A lightweight agent that can be installed on any Windows Server and is used to connect to on-premises Active Directory for user provisioning, deprovisioning, and authentication requests.
- Okta Integrated Windows Authentication (IWA) Web Application: A lightweight web application that is installed on an IIS and is used to authenticate domain users via Integrated Windows Authentication.
- Okta Active Directory Password Sync Agent: A lightweight agent installed on your domain controllers that will automatically synchronize AD password changes, send to Okta, and keep your user’s AD passwords in sync with the apps they use.
- For LDAP integration, Okta provides a single lightweight and secure on-premises component:
- Okta LDAP Agent: A lightweight agent that can be installed on any Windows Server and is used to connect to on-premises LDAP user stores for provisioning, de-provisioning, and authentication requests.
- Simple and Secure Setup and Configuration
- DelAuth, and JIT are turned on by default.
- Users can immediately JIT in without any previous import (because of DelAuth)
- On every DelAuth or JIT request, Group memberships are also imported.
- Users are fully updated on every login and asynchronously.
- Admins can change OUs, user profile and group information in AD and users will be fully updated in Okta.
- DelAuth, and JIT are turned on by default.
- Real Time Synchronization
- Sync when authN.
- Group memberships are imported in addition to the full User profile.
- JIT User Provisioning
- Possible of automatic user account creation in Okta the first time a user authenticates with:
- Active Directory (AD) Delegated Authentication
- Desktop SSO
- Inbound SAML
- JIT updates the accounts of existing end users during full imports.
- This means that end users who are confirmed on the import results page, regardless of whether or not they were subsequently activated, are not eligible for JIT activation.
- When JIT is enabled, users do not receive activation emails.
- If delegated authentication is enabled,
- Yes, no need to import users from AD first for JIT provisioning to create Okta accounts.
- No, then must import the AD accounts first, and they must appear on the imported users list for JIT provisioning to create Okta accounts.
- Possible of automatic user account creation in Okta the first time a user authenticates with:
- Delegated Authentication
- AuthN at AD and it says YES or NO response for authN request.
- Desktop Single Sign-On
- Self Service Password Reset Support
- Updates both AD and Okta password for a user.
- Security Group (SG) –Driven Provisioning
- Bulk provisioning/ deprovisioning possible.
- Deprovisioning
- SSO for Authenticated Apps resides inside On-prem
- SSO to local AD apps using SWA after authN with Okta (IdP-init)
AD config in Okta
By default Okta uses the Okta user profile user name during delegated authentication. For example, if the AD app-user user name is samAccountName (domain\jdoe) and the Okta user profile user name (login field) is UPN, then Okta use UPN (jdoe@domain.com) to log in the user.
Okta username format — The username format you select must match the format you used when you first imported users. Changing the value can cause errors for existing users. Choose one of the following options:
- Custom — Select this option to use a custom user name to sign in to Okta. Enter the Okta expression language to define the Okta user name format. To validate your mapping expression, enter a user name and click the view icon.
- Email address — Select this option to use an email address for the Okta user name.
- SAM Account name — Select this option to combine the SAM Account Name and the AD domain to generate the Okta username. For example, if the SAM Account Name is jdoe and the AD domain is mycompany.okta.com, then the Okta username is jdoe@mycompany.okta.com.
- SAM Account name + Configurable Suffix — Select this option to combine the SAM Account Name and a configurable suffix to create the Okta user name. When using this option, do not include the @ character before the Configurable Domain.
- User Principal Name (UPN) — Select this option to use the UPN from AD to create the Okta user name.
Note: All Okta users can sign in by entering the alias part of their user names as long as it maps to a single user in your organization. For example, jdoe@mycompany.okta.com could sign in using jdoe.
USG support — Select Universal Security Group Support to ignore domain boundaries when importing group memberships for your end users. This assumes that the relevant domains are connected in Okta. You must also deploy an AD agent for every domain in your forest that contains the USG object that you want to sync with Okta. Each connected domain then imports its groups. When a user’s group memberships match any groups that were imported (from any connected domain in the forest), Okta syncs the memberships for the user to each group. Only groups from connected domains are imported. This setting requires JIT provisioning.
Max Import Unassignment — Click edit to modify the value that the number of app unassignments stops. The default is 20%. This action prevents accidental loss of user accounts. This setting affects all apps with imports enabled. See Import safeguards.
Desktop Single Sign-On (DSSO)
Allow users to log in to their AD-connected computer and extend that Single Sign-On (SSO) experience through to Okta.
- This means that logging into a user’s Windows machine gives them direct access to their Okta-configured applications, and reduces the number of logins needed to access both company and cloud-based applications to one.
- The AD-version of this is also known as Integrated Windows Authentication (IWA).
- Download and install Okta’s IWA web application, configure the relevant IP ranges, and the setup is complete.
- DSSO is not supported for LDAP.
Two methodologies are available for DSSO implementation:
- Agentless (recommended)
- IWA web agent running on premises
Agentless Desktop Single Sign-on – uses Kerberos
- You have an Active Directory domain (or multiple domains) integrated with your Okta org.
- In order for Okta to negotiate Kerberos authentication for agentless DSSO, you need to create a new service account and set a Service Principal Name (SPN) for that service account. This will delegate Kerberos authentication to external service, rather internal Windows Kerberos authentication.
setspn -S HTTP/<myorg>.kerberos.<okta|oktapreview|okta-emea>.com <ServiceAccountName>>
- Where HTTP/<myorg>.kerberos.okta.com is the SPN. <ServiceAccountName> is the value you used when configuring the Early Access version of Agentless DSSO and <oktaorg> is your Okta org (either oktapreview, okta-emea or okta). For example,
setspn -S HTTP/atko.kerberos.oktapreview.com atkospnadmin.

Okta IWA Web agent for Desktop Single Sign-on
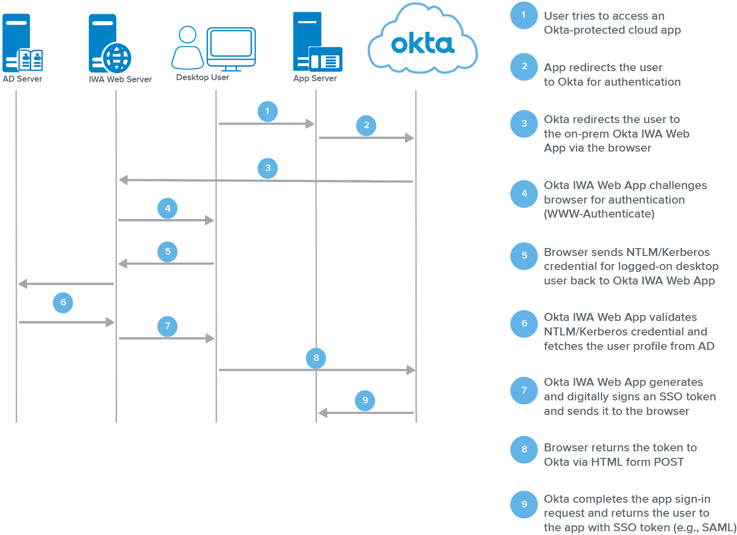
Flow 1:
Flow 2:
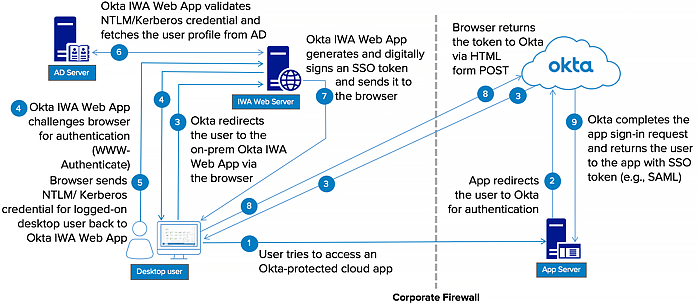
In simple steps:
- User navigates to https://mycompany.okta.com.
- The user is redirected to the locally installed IWA web application.
- The IWA web application transparently authenticates the user via Integrated Windows Authentication (Kerberos).
- The user is redirected back to the Okta login page with cryptographically signed assertions containing his AD user identity.
- The Okta service validates the signed assertions and sends the user directly to his Okta home page.

Advanced Server Access (Zero Trust)
- Zero Trust has emerged as the right architecture for the modern cloud (AWS, GCP, Azure).
- This changes the access model significantly, shifting controls from the network layer to the application layer.
- ASA is an application that manages SSH and RDP access to Linux and Windows servers.
- Using Okta as its source of truth, ASA reconciles with your internal servers to provide Zero Trust software that you can use to secure them.
- Team is a named group of users who can authenticate with Okta.
- A team is an ASA tenant, which is similar to an Okta tenant.
- All configurations and resources in ASA are scoped to a team.
- Project is like AWS account.
- Each Project contains resources like EC2, Redis server, etc.
- Dynamic Credentials: Think of Projects as programmable Certificate Authorities which issue ephemeral certificates in accordance with your RBAC configurations.
- Each of these certificates contains at least the following information:
- Project for which the certificate was issued
- Time at which the certificate expires
- Username to be used on the server of the ASA user to whom the certificate was issued
- Since Advanced Server Access credentials are short-lived, and scoped to a project, even if a credential is compromised by an attacker, the attacker has a very limited window of time to use the certificate before it expires, and it is only of use against resources in that project.
- Services
- Services allow you to authenticate and login to servers using a service user. This enables you to leverage the security of ephemeral certificates when building automation that requires access to remote servers.

Unifying your policies around identity sets the foundation to extend smarter access controls.
- Identity sets foundation -> so that Policies can be clearly attributed and audited towards users/ roles.
- Identity drives security -> so that it provides centralized access control heterogeneous envs (on-prem, clouds).
- Identity defines experience -> so that it automates the lifecycle of identity from end-to-end.
ASA is identity-first access management for servers.
- Client application is installed on users’ workstations to interact with their local SSH tools and communicate with Okta service.
- Comes with CLI (is stf – ScaleFT) option to perform operations like signin to Okta-ASA, list servers to login to particular server, server/ device-info etc).
- Server Agent enrolled with Okta that manages the local users, groups, and entitlements and also captures all login events for audit purposes.
- Administrators manages collection of servers associated to RBAC as Projects.
- Projects is an authorization scope of who can access which servers and what tasks within servers they can perform.
- Each Project is a dedicated CA (Certificate Authority) minting Ephemeral certificates.
- Users (UID) and Groups (GID) can assign to Projects to grant access to the servers.
- Groups can have pseudo access (r-w-x).
- These are visual representation of user/ group in actual servers.
- Entitlement is a whitelist of specific commands/ tasks that Users in Group can perform. (eg : web-team group can only run restart-apache, but not restart the DB).
- Comes with CLI (is stfd):
- /etc/passwd -> user-group accounts data
- /etc/sudoers -> admin accounts data
- /etc/sudoers.d -> entitlement data
- Server agents is regularly interacts with Okta servers for any update to user status, group membership or entitlements.
- If user is inactive in Okta, Server agent will update the status in local server and disable the account locally as well.
- Server Agent is deployed using Terraform script along with other necessary steps in deploying servers (EC2 instance) in IAAS cloud.
- Enrollment Token is needed to to install/ enroll the Server Agent to communicate to Okta.
- Once enrollment finishes, Server Agent will bring users, groups, entitlements to provision these locally in the servers.
- Finally, configure the SSH-server to locally trust the client-certificate (Ephemeral cert) issued by Project as a CA (specific to defined ASA Project)

- A user logs into a server directly from their local SSH tools, which is integrated with the SSH Client Application.
- Every login is independently authenticated via Okta, subject to the Sign-On policies you specify and then authorized against the role based access associated with the target server.
- When access is granted, Project mints a short-lived client certificate scoped to the user, device, and project the server belongs to.
- This certificate is delivered to the SSH Client Application, which uses it to initiate a secure session with the target server via SSH.
- The Server Agent captures the login event and delivers to the backend for auditing purposes, or you can stream to your own logging service.
Ephemeral Credential is:
- Given only authenticated/ authorized for independent login request
- On-demand
- Tightly scoped
- Expires in minutes
- Self revoke after single use
While other products and practices focus so much of their effort on “protecting the keys,” this is the best way to mitigate the risk of credential theft is to render them useless.
With a solid identity foundation in Okta, you can support a wide range of access management use cases. Advanced Server Access brings seamless controls to the infrastructure layer in an elegant manner.

WAM
There are three main ways to secure enterprise web apps:
- Standalone security
- Kerberos
- WAM
- In WAM, it was determined that most application requests passed through routing and balancing in the multi-tier architecture.
- So, a decision was made to take advantage of that fact and enforce authentication and authorization at this level to validate access.
WAM Responsibilities
- Authentication
- Authorization
- Session Management
WAM Integration Patterns
In order to authenticate and authorize an app, WAM solutions must be integrated with the app they secure:
- Header-Based Authentication
- Applications are protected by an HTTP server with a WAM Policy Enforcement Point agent, or PEP agent that sits in between the user and the app.
- After the user is authenticated, the WAM agent injects information about the user on the request (HTTP Header Variable).
- This is the most common standard used in WAM.
- For example, 95% of Oracle Access Manager apps are protected using this standard by Oracle WebGate.
- Header-based auth typically utilizes an enforcement point to examine all the traffic coming to the HTTP server either by utilizing.
- App server plugin (Agent)
- Users access the application directly. The server that hosts the application will talk directly to the WAM server to validate the user access before granting access to the application.
- This model is usually available on Java application servers such as WebLogic and WebSphere.
- HTTP Server or (Agent)
- The HTTP Plugin sits on the Routing and Balancing layer in the DMZ on the web server itself.
- Examples of some web servers are OHS, Apache, IIS, and NGINX.
- Parallel gateway or Reverse proxy engine
- Instead of using an agent plugin on each web application, many WAM solutions deploy gateway servers to intercept and inspect requests to the web application.
- The gateway can then insert identity headers into the request for the application to read. This is the architecture of the Okta Access Gateway. This is similar to Oracle Webgates.
- App server plugin (Agent)

- Kerberos
- This type of integration relies on tickets granted by a Kerberos Ticket Granting Service in order to allow traffic.
- This pattern is typically used in Windows environments, apps hosted on IIS, and on-prem SharePoint.
- Secure Form Fill
- Applications are protected by an HTTP server that sits in between the user and the app (similar to header-based authentication).
- However, after the user is authenticated, the WAM solution will automatically sign into the enterprise application using a login and password.
- This is similar to what we have with Okta’s Secure Web Authentication (SWA).
- However, the password manipulation happens on the server side.
- Okta supports both client and server sides.
- SAML / WS-Fed / OIDC
- This is the same model used in Okta for authentication into cloud apps.
- The major difference between Okta and WAM, is that configuring federation in WAM can be super complex.
- SDK
- Proprietary vendor toolkit that enables ISVs to build their own integrations.
- Proprietary vendor toolkit that enables ISVs to build their own integrations.

Flow:
- User accesses a web application. A Load Balancer routes the request to the proper server.
- A plugin or agent integrated to the app or HTTP server (also known as Policy Enforcement Point – PEP) intercepts the request and validates the access with the SSO Server (also known as Policy Decision Point, or PDP) using a proprietary protocol (dotted green lines).
- The SSO Server validates the user session and the resource (URL) requested. During authentication, it also validates the user credentials against an LDAP server.
- Upon the SSO Server approval, the Agent complements the request context with information about the logged user – i.e., the user login – for the enterprise application. Agents embedded within the application pass the user information in session while agents used with HTTP servers send this information through HTTP Headers.
- The enterprise application extracts the user information from the HTTP headers or the session, process the request, and returns a response to the end user.
Components:
- Load Balancer: Balances traffic between Applications and HTTP Servers.
- Examples: Big-IP F5, Apache with mod_proxy and mod_proxy_balancer, and Cisco ACE.
- Policy Enforcement Point (PEP): Agent or plugin that implements authentication on enterprise applications. Includes:
- Application/ERP/Custom Agents: These PEPs are installed directly in Application Servers, ERPs/CRMs, and as proprietary SDKs for direct use in applications.
- Examples: Oracle OAM Access SDK, Oracle AccessGate for eBusiness Suite, Oracle OSSO Plugin, OAM Authenticator Provider for WebLogic, CA Application Server Agent for Tomcat, WebSphere, JBoss, and WebLogic, SiteMinder Agent SDK, SiteMinder ERP Agents for SAP, PeopleSoft, Siebel, and Tivoli Manager for WebSphere.
- Web Agents or Web Gateways: These PEPs are provided as software appliances or as plugins for HTTP Servers such as Apache and IIS.
- Examples: Oracle WebGate, IBM WebSeal, Tivoli Apache Plugin, CA SSO Apache Plugin, CA SiteMinder Gateway, Novell Access Gateway
- Application/ERP/Custom Agents: These PEPs are installed directly in Application Servers, ERPs/CRMs, and as proprietary SDKs for direct use in applications.
- HTTP Server(s): Serves HTTP requests.
- Examples: OHS, Apache, IIS, and NGINX.
- SSO Server or Policy Decision Point (PDP): The SSO Server validates users, URLs, and URIs to authenticate and authorize access.
- Examples: CA SiteMinder, Oracle Access Manager (OAM), Tivoli Access Manager (TAM), and Novell Access Manager (NAM).
- User Directory Store (LDAP): A directory containing user credentials for authentication.
- Examples: Oracle Directories (OID, OUD, and OVD), Sun Directory Server (Sun DS or ODSEE), Tivoli Directory Manager, OpenLDAP, and Novell eDirectory
- Firewalls: Network solutions used for segmenting traffic between WAM components. The network segmentation is required to avoid unauthorized access to enterprise apps and to avoid traffic sniffing or spoofing.
- Enterprise Applications: Applications protected by the IdM solution. Enterprise apps receive requests with the user information as session arguments or via HTTP headers.
Okta Access Gateway
- Okta Access Gateway is a reverse proxy solution that is designed to secure web applications that do not natively support SAML or OIDC.
- Access Gateway integrates with legacy applications through the use of:
- HTTP Headers
- URL-based authorization
- Kerberos Tokens
- Access Gateway allows you to seamlessy integrate your legacy web based applications with Okta’s Cloud SSO Capabilities.
- Access Gateway is an ideal solution for any Okta customer where:
- Enterprise wants to unify all IAM under an Okta platform, but requires integration with web applications that do not support federation (SAML, WS-Fed).
- Vendors, customers, or partners must access your internal business web applications (such as SharePoint, Oracle E-Business Suite, and others) from the internet.
- Must restrict unauthorized network access to your web applications.
- Enterprise has web applications that lack a native authentication mechanism.
- Company is looking for a cost-effective replacement for your on-premise WAM solution.
- Supports Web (HTTP/HTTPS) based applications ONLY.
- Supports both SP and IdP-init SSO (from Okta dashboard). No IdP-init SSO in WAM.

Modern (Cloud and Mobile) applications flow
- A. User accesses a cloud or mobile application.
- B. The app validates the session. If there’s no session, it redirects the user for a federated authentication in Okta.
- C. Okta authenticates the user using the native identity functions: Single Sign-On, User Directory Store, Adaptive MFA, and Federation.
- D. Upon access approval, the user is redirected back to the Cloud of Mobile App. The app completes the federation process, establishes the user session, and responds to the user request.
Enterprise Applications flow
- User accesses web application via HTTPS.
- The Access Gateway intercepts the user request. If the session is invalid, it redirects the user for a federated authentication on Okta.
- Okta authenticates the user. All the identity functions (Single Sign-On, User Directory Store, Adaptive MFA, and Federation) are built natively into the Identity Platform.
- Upon access approval, the user is redirected back to the Access Gateway that completes the federation. Because the gateway is capable of working with different kinds of applications, it doesn’t require native integration.
- The enterprise app captures the user information, process, and responds to the request.
Components
- Okta: Okta provides Single Sign-On, Adaptive Multi-Factor Authentication, API Authorization, User Directory, Account Provisioning, and Federation in the cloud for modern apps (via native standards-based integrations) and enterprise apps (via Access Gateway).
- Cloud and Mobile Applications: Modern applications with direct access to the internet.
- Access Gateway: The Okta Access Gateway bridges the gap between the Identity Platform and your enterprise applications. It leverages federated authentication for Single Sign-On and Adaptive MFA and connects to your enterprise application using WAM standards (such as security headers). Because the gateway supports different types of applications, it doesn’t require native integration.
- Firewalls: Network solutions used for segmenting traffic between components. The network segmentation is still required to avoid unauthorized access to enterprise apps and to avoid traffic sniffing or spoofing.
- Enterprise applications: Applications protected by the gateway. Enterprise applications receive traffic via HTTP Server with the user information on the HTTP headers.


- Okta Tenant
- Virtualization Environment
- Virtual Appliance (OAG)
- Protected Applications
Using a reverse-proxy architecture, Okta’s Access Gateway delivers: SSO and Adaptive-MFA from the cloud to on-prem apps without changing how those apps work.
Access Gateway uses a VM deployment model, you can run either on-prem using solutions like VMWare Hypervisor or Virtual Box or even deploy on your IaaS provider of choice from RackSpace to Amazon AWS.

Access Gateway Supported Applications
- Sample Cookie -> pass data via HTTP cookies
- Sample Header -> pass data via HTTP headers
- Sample Policy -> uses URL-based policy to restrict access to apps
- Sample Proxy -> OAG act as proxy for apps
- Header Based -> provide SSO via HTTP headers to apps
- No-auth -> reverse-proxied by OAG without any authentication
- OAM/ Orcl apps -> provide SSO via HTTP headers to Orcl apps
- Microsoft-IWA -> for MSFT Kerberos based back end applications
- SFDC -> SSO for SFDC apps




- Deploy Okta
- Integrate Okta to LDAP/ AD using Agent
- Deploy Okta login page
- Configure SAML from Okta to WAM (OAM) for SSO
- Move SAML Apps to Okta
- Deploy OAG
- Enable OAG to secure App (which uses agents directly not reverse-proxy, OHS) and remove agents
- Repeat until all Apps are migrated
- Remove WAM’s HTTP Server (OHS)
- Remove Okta to WAM SAML (OAM)
- Remove WAM (OAM)
- Optional: Migrate users to UD and remove LDAP
- Optional: Migrate Apps to use Okta natively

















