- High Availability Tools
- ELB
- E-IP address (thru IP masking)
- Route 53
- CloudFront
- Auto Scaling
- CloudWatch
- Fault-Tolerant Tools
- SQS
- S3
- RDS (read replica)
- AWS Managed Services (AMS):
- S3
- RDS
- Redshift
- DynamoDB
- CloudFront
- ELB
- Lambda
- Elastic File System
- Elastic Transcoder
- SES
- WorkSpaces
- CloudSearch
- Elastic MapReduce?
- Serverless Services:
- Lambda
- DynamoDB
- ECS (through Fargate)
- Server-based Services:
- EC2
- RDS
- Redshift
- EMR
- EBS for EC2 and RDS.
- EFS for big data and varied use cases.
- Avoid single point of failure (SPOF) achieved through ELB, Auto Scaling, Route53, EC2 auto-recovery, OpsWorks (configuration management service; chef/ puppet) and Elastic Beanstalk.
- Customers should be aware that their responsibilities may vary depending on the AWS services chosen.
- EC2, you are responsible for applying OS and security patches.
- RDS, AWS is responsible for the same.
- Support Concierge Team (via Enterprise Support plan) are AWS billing and account experts.
- 24 x7 access to AWS billing and account inquires.
- Guidance and best practices for billing allocation, reporting, consolidation of accounts, and root-level account security.
- Access to Enterprise account specialists for payment inquiries, training on specific cost reporting, assistance with service limits, and bulk purchases.
- AWS Abuse team can assist you when AWS resources are being used to engage in the following types of abusive behavior:
- I. Spam: You are receiving unwanted emails from an AWS-owned IP address, or AWS resources are being used to spam websites or forums.
- II. Port scanning: Your logs show that one or more AWS-owned IP addresses are sending packets to multiple ports on your server, and you believe this is an attempt to discover unsecured ports.
- III. Denial of service attacks (DOS): Your logs show that one or more AWS-owned IP addresses are being used to flood ports on your resources with packets, and you believe this is an attempt to overwhelm or crash your server or software running on your server.
- IV. Intrusion attempts: Your logs show that one or more AWS-owned IP addresses are being used to attempt to log in to your resources.
- V. Hosting objectionable or copyrighted content: You have evidence that AWS resources are being used to host or distribute illegal content or distribute copyrighted content without the consent of the copyright holder.
- VI. Distributing malware: You have evidence that AWS resources are being used to distribute software that was knowingly created to compromise or cause harm to computers or machines on which it is installed.
- AWS Security team is responsible for the security of services offered by AWS.
- AWS Customer Service team is at the forefront of this transformational technology assisting a global list of customers that are taking advantage of a growing set of services and features to run their mission-critical applications. The team helps AWS customers understand what Cloud Computing is all about, and whether it can be useful for their business needs.
- AWS Infrastructure Event Management is a short-term engagement with AWS Support, included in the Enterprise-level Support product offering, and available for additional purchase for Business-level Support subscribers. AWS Infrastructure Event Management partners with your technical and project resources to gain a deep understanding of your use case and provide architectural and scaling guidance for an event. Common use-case examples for AWS Event Management include advertising launches, new product launches, and infrastructure migrations to AWS. Helps architectural and scaling guidance.
- AWS Personal Health Dashboard provides alerts and remediation guidance when AWS is experiencing events that may impact you. While the Service Health Dashboard displays the general status of AWS services, Personal Health Dashboard gives you a personalized view into the performance and availability of the AWS services underlying your AWS resources. The benefits of the AWS personal health dashboard include:
- Personalized View of Service Health
- Proactive Notifications
- Detailed Troubleshooting Guidance
- Shared Controls: Both AWS and customers responsible for on their own layers:
- Patch Management – AWS is responsible for patching and fixing flaws within the infrastructure, but customers are responsible for patching their guest OS and applications.
- Configuration Management – AWS maintains the configuration of its infrastructure devices, but a customer is responsible for configuring their own guest operating systems, databases, and applications.
- Awareness & Training – AWS trains AWS employees, but a customer must train their own employees.
- Inherited Controls: Customer fully inherits physical controls and environmental controls from AWS.
- AWS Artifact is a self-service audit artifact retrieval portal that provides our customers with on-demand access to AWS’ compliance documentation and AWS agreements. You can use AWS Artifact Reports to download AWS security and compliance documents, such as AWS ISO certifications, Payment Card Industry (PCI), and System and Organization Control (SOC) reports. You can use AWS Artifact Agreements to review, accept, and track the status of AWS agreements such as the Business Associate Addendum (BAA).
- “Pay as you go” – On-demand
- “Save when you reserve” – Upfront and discounted hourly rate.
- “Pay less as AWS grows” or “AWS Economies of Scale” – Discounts that you get over time as AWS grows. For example, AWS has reduced the per GB storage price of S3 by 80% since the service was first introduced in 2006.
- “Pay less by using more” – Volume based discounts and as your usage increases. For services such as S3, pricing is tiered, meaning the more you use, the less you pay per GB.
- S3 Transfer Acceleration enables fast, easy, and secure transfers of files over long distances between your client and an S3 bucket. Transfer Acceleration takes advantage of Amazon CloudFront’s globally distributed edge locations. As the data arrives at an edge location, data is routed to Amazon S3 over an optimized network path.
- RDS Read Replicas provide enhanced performance and durability for database (DB) instances. Avoid SPOF, disaster recovery capabilities and allows you to scale out globally.
- RDS is multi-AZ.
- RDS Aurora is multi-region (include multi-AZ). Aurora is up to 5 times faster than standard MySQL databases and 3 times faster than standard PostgreSQL db.
- Security scales with your AWS Cloud usage. No matter the size of your business, the AWS infrastructure is designed to keep your data safe.
- APN Consulting Partners : responsible for complete DT from on-prem to AWS.
- APN Technology Partners: F5, MSFT are tech partners to AWS.
- AWS Professional Services: Work on specific outcomes related to enterprise cloud adoption. Accenture helps to do one specific cloud adoption and not complete DT.
- Created the AWS Cloud Adoption Framework (AWS CAF) to help organizations design and travel an accelerated path to successful cloud adoption.
- Technical Account Manager (TAM) : technical point of contact who provides advocacy and guidance to help plan and build solutions using best practices and proactively keep your AWS environment operationally healthy. TAM is available only for the Enterprise support plan.
- Service Limits:
- Monitor SL using Trusted Advisor
- AWS maintains service limits for each account to help guarantee the availability of AWS resources, as well as to minimize billing risks for new customers. Some service limits are raised automatically over time as you use AWS, though most AWS services require that you request limit increases manually. Most service limit increases can be requested through the AWS Support Center by choosing Create Case and then choosing Service Limit Increase.
- Data in Transit protection by using SSL or by using client-side encryption.
- Data in Rest protection by using server-side encryption.
- AWS Management console: user name or password.
- AWS API: API token.
- AWS SDK: Access key ID and secret access key.
- AWS CLI: Private/ Public Key pair.
- CloudFormation and Auto Scaling are free to use but provisioned resources are charged.
- Quick Start is a CF template by technology partners. F5-BigIP CF template helps to install BigIP instance in AWS.
- CloudWatch Logs aggregates, monitor, store, and access your log files from EC2 instances, CloudTrail, Route 53, and other sources.
- Right DB tech based on # of R/ W ops, data storage, data source, latency, throughput, data model, and nature of queries.
- Tagging: Logical groupings of resources based on organizationally relevant dimensions, project, Cost center, Development environment, Application or Department. For example, if you tag resources with an application name, you can track the total cost of a single application that runs on those resources.
- Tagging best practices:
- Always use a standardized, case-sensitive format for tags, and implement it consistently across all resource types.
- Consider tag dimensions that support the ability to manage resource access control, cost tracking, automation, and organization.
- Implement automated tools to help manage resource tags.
- Err on the side of using too many tags rather than too few tags.
- Remember that it is easy to modify tags to accommodate changing business requirements, however consider the ramifications of future changes, especially in relation to tag-based access control, automation, or upstream billing reports.
- Usages:
- Visualize information about tagged resources in one place, in conjunction with Resource Groups.
- View billing information using Cost Explorer and the AWS Cost and Usage report.
- Send notifications about spending limits using AWS Budgets.
- AWS Config, you can discover existing and deleted AWS resources, determine your overall compliance against rules, and dive into configuration details of a resource at any point in time. These capabilities enable compliance auditing, security analysis, resource change tracking, and troubleshooting.
- To save AWS cost:
- Terminate all unused EC2 instances.
- Delete all the EBS volumes attached to them.
- Release the un-utilized Elastic IPs.
- Delete the ELBs.
- Decommissioning process: Use DoD 5220.22-M (“National Industrial Security Program Operating Manual “) or NIST 800-88 (“Guidelines for Media Sanitization”) to destroy data as part of the decommissioning process.
- AWS Application Discovery Service helps systems integrators quickly and reliably plan application migration projects by automatically identifying applications running in on-premises data centers, their associated dependencies, and their performance profiles.
- You can use a server certificate provided by AWS Certificate Manager (ACM) or one that you obtained from an external provider.
- Use ACM or IAM to store and deploy server certificates.
- Use IAM as a certificate manager only when you must support HTTPS connections in a region that is not supported by ACM.
- IAM supports deploying server certificates in all regions, but you must obtain your certificate from an external provider for use with AWS.
- Route 53 is not responsible for creating SSL certifications.
- When selling a reserved instance on the Amazon EC2 Reserved Instance Marketplace, you only have the option to set an upfront price for the instance.
- Bootstrapping: Custom code or script to install required s/w or copy resource or define resource state (prod, dev, test). Same script used for all deployments.
- Golden Images: a snapshot of a particular state of that resource. When compared to the bootstrapping approach, a golden image results in faster start times and removes dependencies to configuration services or third-party repositories. This is important in auto-scaled environments where you want to be able to quickly and reliably launch additional resources as a response to demand changes.
- Non-explicit deny: When a new IAM user is created, that user has NO access to any AWS service. Use allowed via IAM permission and access policies.
- Global Tables builds upon DynamoDB’s global footprint to provide you with a fully managed, multi-region, and multi-master database that provides fast, local, read and write performance for massively scaled, global applications.
- EC2 Cost factor:
- Compute
- Storage
- Data Transfer Out
- Resource Groups:
- Create a custom console that organizes and consolidates information based on your project and the resources that you use.
- AWS Management Console is organized by AWS service.
- Amazon DynamoDB Accelerator (DAX) is a fully managed, highly available, in-memory cache for DynamoDB that delivers performance improvements from milliseconds to microseconds – even at millions of requests per second. DAX adds in-memory acceleration to your DynamoDB tables without requiring you to manage cache invalidation, data population, or cluster management.
- Reservation models for stable applications:
- EC2 reserved instances
- RDS reserved instances
- DynamoDB Reserved Capacity (capacity means latency and throughput)
- ElasticCache Reserved Nodes
- Redshift Reserved Nodes
- Amazon ElasticCache for Redis is a blazing fast in-memory data store that provides sub-millisecond latency to power internet-scale real-time applications.
- AWS IAM console or AWS CLI to enable a virtual MFA device for an IAM user.
- AWS strongly recommend that you DON’T use AWS account root user for your everyday tasks, even the administrative ones. AWS account root user perform only a few account and service management tasks.Use the root user only to create your first IAM user with administrative privileges, and use this Admin user for all your work. Event on root account compromised.
- Change the user name and the password of the root user account and all of the IAM accounts that the administrator has access to.
- Rotate (change) all access keys for those accounts.
- Enable MFA on those accounts.
- Put IP restriction on all Users’ accounts.
- OpsWorks and Elastic Beanstalk automatically restarts resources after terminating.
- You can find a paid AMI using the EC2 console, AWS Marketplace and AWS CLI.
- Amazon DevPay is a simple-to-use online billing and account management service that makes it easy for businesses to sell apps built on, or run on top of AWS.
- AWS free security resources include AWS Security Blog, Security Bulletins, Provable Security, Whitepapers, Advanced Innovation, Developer Documents, Articles and Tutorials, Training, Compliance Resources and Testimonials.
AWS Terms
| Sno | Definitions | Explanations |
| 1 | Region | Global Infra – Geographic region where AWS located. |
| 2 | AZ |
|
| 3 | Edge Locations | Global Infra – CDN – A site that CloudFront uses to cache copies of your content for faster delivery to users at any location. |
| 4 | IAM Users | Individuals |
| 5 | IAM Groups | Easy manage users and their access |
| 6 | Resources | S3, EC2, etc. |
| 7 | Roles | Manage resource and temporary authz to resource. |
| 8 | Policies | User/ resource access definitions. The policy is a JSON document that consists of:
|
| 9 | VPC |
|
| 10 | IGW
NAT Gateway |
H/W + S/W based gateway to interact b/w VPC and internet.
In public subnet, to allow private subnet resource to access internet. |
| 11 | Route-Table |
|
| 12 | NACL |
|
| 13 | Security Groups |
|
| 14 | Subnet |
|
| 15 | Public and Private Subnet |
|
| 16 | S3 Buckets |
|
| 17 | S3 Folders | Subfolders of buckets. |
| 18 | S3 Objects | Files within buckets/ folders. |
| 19 | S3 Lifecycle Policy | Rules that change the storage class of S3 objects, |
| 20 | S3 Permissions | A granular control over who can view, access, use specific buckets and objects. |
| 21 | S3 Versioning |
|
| 22 | AMI |
|
| 23 | EBS |
|
| 24 | IOPS |
|
| 25 | Root vs EBS Volumes | Every EC2 must have root volume (gone when EC2 recycled) but additional EBS volume can be added (persist beyond lifetime of EC2). |
| 26 | Snapshots |
|
| 27 | IP Addressing | Provide EC2 with public IP address.
Private IP Address: By default, all EC2 has private IP address which helps to communicate between other EC2 within same VPC. Public IP Address: By default, EC2 can be launched with or without a public IP address. It helps to communicate with internet. |
| 28 | Lightsail | Virtual Private Server (Pod based env) includes VM, SSD-based storage, data transfer, DNS management, and a static IP address. |
| 29 | Polly | ML turns text into lifelike speech |
| 30 | Rekognition | ML; image analyzer |
| 31 | RDS |
|
| 32 | DynamoDB |
|
| 33 | DB Migration Service | Migrate or replicate your existing databases to RDS. |
| 34 | SSH Tunneling |
|
| 35 | Systems Manager | Gives visibility and control of your infrastructure on AWS. Supports tools:
|
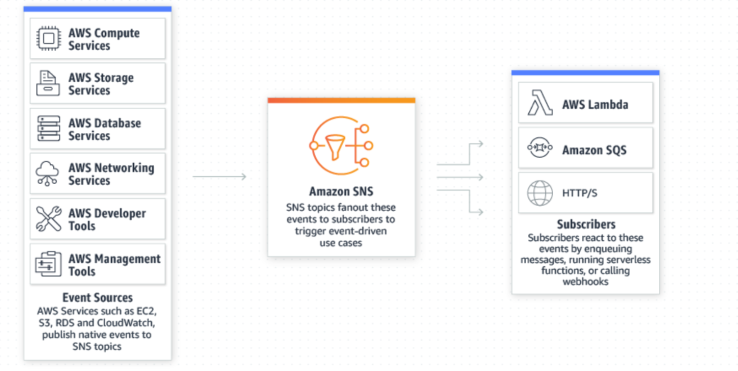
| 36 | SNS | Async Pub/ Sub messaging and mobile notification services supports Amazon SQS, HTTP/S, email, Lambda, SMS, APN, Google push notification. |
| 37 | Topics | Labeling/ grouping of different endpoints that you send messages to. |
| 38 | Publishers | Human/ alarm/ event that triggers the messages to be sent. |
| 39 | Subscribers | Endpoints that a topic sends messages to (i.e. email address, phone). |
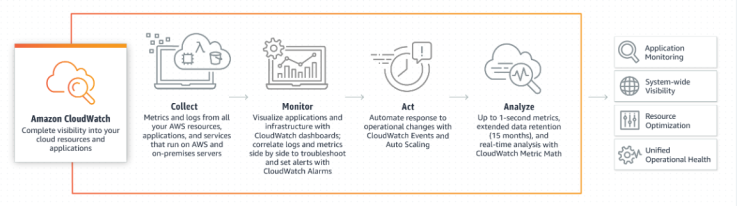
| 40 | CloudWatch |
|
| 41 | CloudWatch Thresholds | Maximum allowed value to not trigger an alarm. |
| 42 | CloudWatch Alarms |
|
| 43 | CloudWatch Dashboard | To view resource metrics (EC2 CPU Util, S3 bucket size, Billings over-limit) |
| 44 | CloudWatch Events | Events provides a near real-time stream of system events that describe changes to AWS. |
| 45 | CloudWatch Rules |
|
| 46 | CloudWatch Log Insights | Enables to drive actionable intelligence from logs to address operational issues without needing to provision servers or manage software. |
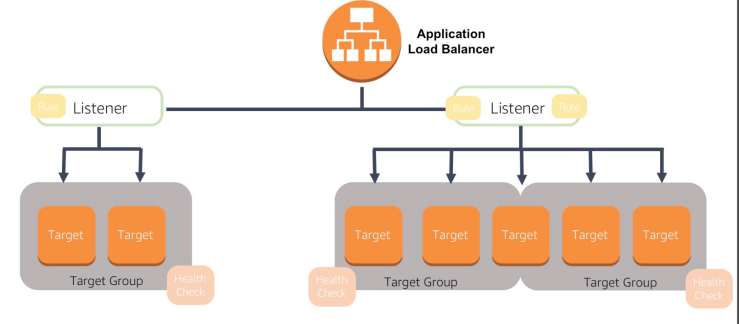
| 47 | ELB |
|
| 48 | Application LB |
|
| 49 | Network LB |
|
| 50 | Classic LB |
|
| 51 | LB Health Check | Checks the health of EC2 by HTTP or TCP pings with Response Timeout/ Interval/ Unhealthy and Healthy Threshold. |
| 52 | Load Balancer Capacity Unit (LCU) | Based on the highest usage dimension of one of the following:
|
| 53 | Auto Scaling |
|
| 54 | Auto Scaling Groups |
|
| 55 | Auto Scaling Launch Configuration | EC2 template used when Auto Scaling needs to add additional server to AS Group when required (can add bootstrap script and other configurations to start instances). |
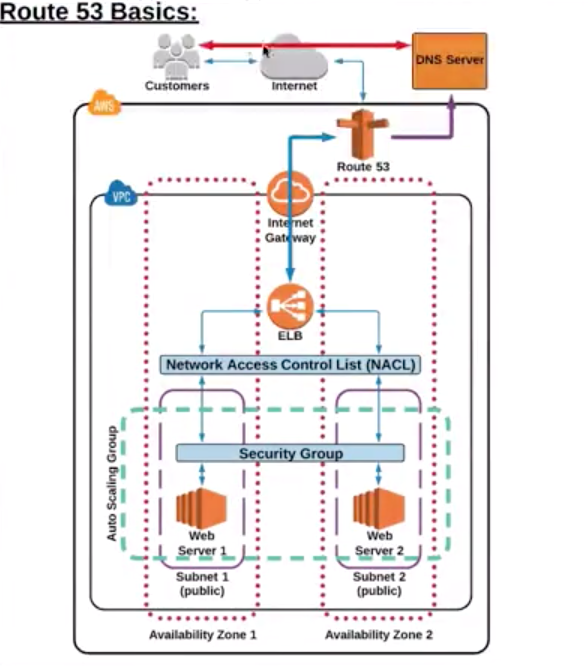
| 56 | Route 53 |
|
| 57 | Hosted Zones | Registered domain path routes information and its IP address.
|
| 58 | Record Sets | Information about the resource record. |
| 59 | Lambda |
|
| 60 | Instance Purchasing Options | Options to purchase EC2 instances. |
| 61 | EC2 – On-Demand Instances | Pay, by the second, for the instances that you launch. Expensive. |
| 62 | EC2 – Reserved Instances |
|
| 63 | EC2 – Scheduled Instances | Purchase instances that are always available on the specified recurring schedule, for a one-year term. |
| 64 | EC2 – Spot Instances | Request unused EC2 instances, which can lower your Amazon EC2 costs significantly (90%). |
| 65 | EC2 – Dedicated Hosts | Pay for a physical host that is fully dedicated to running instances, and bring existing per-socket, per-core, or per-VM software licenses to reduce costs. |
| 66 | EC2 – Dedicated Instances | Pay, by the hour, for instances that run on single-tenant hardware. Share dedicated rack space within server host. |
| 67 | EC2 – Capacity Reservations |
|
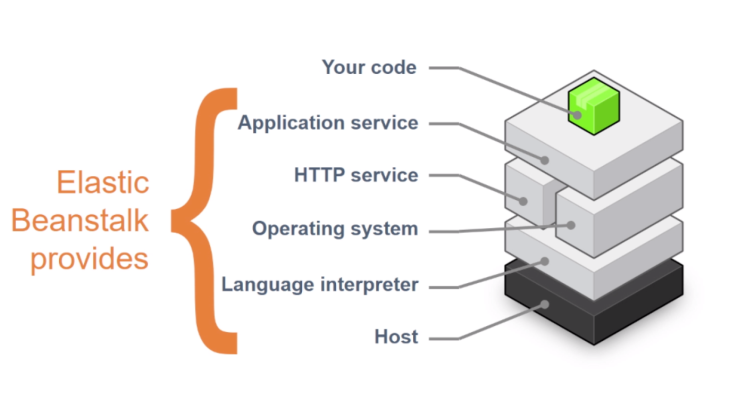
| 68 | Elastic Beanstalk |
|
| 69 | CloudFront |
|
| 70 | CloudTrail |
|
| 71 | CloudFormation |
|
| 72 | DB tools |
|
| 73 | Shield |
|
| 74 | Trusted Advisor |
|
| 75 | Support Plans |
|
| 76 | ECS |
|
| 77 | Fargate |
|
| 78 | Redshift |
|
| 79 | X-Ray |
|
| 80 | Dev tools |
|
| 81 | Snowball |
|
| 82 | Storage Gateway |
|
| 83 | Cognito | Lets you add user sign-up, sign-in, and access control to your web and mobile apps using social and enterprise logins. |
| 84 | Directory Services |
|
| 85 | GuardDuty |
|
| 86 | Macie |
|
| 87 | KMS |
|
| 88 | Inspector |
|
| 89 | SageMaker |
|
| 90 | API Gateway |
|
| 91 | WorkMail | WorkMail is a secure, managed business email and calendar service with support for existing desktop and mobile email client applications. Uses IMAP protocol (receive email; stores in server and client). |
| 92 | SES | Simple Email Service (Amazon SES) is a cloud-based email sending service designed to help digital marketers and application developers send marketing, notification, and transactional emails. Uses SMTP protocol (sent emails). |
| 93 | SQS |
|
| 94 | SWF |
|
| 95 | EMR |
|
| 96 | ElasticSearch |
|
| 97 | Data Lake | A data lake is a storage repository (flat architecture instead of hierarchical fashion) that holds a vast amount of raw data in its native format until it is needed. |
| 98 | Lake Formation |
|
| 99 | ElasticCache |
|
| 100 | OpsWorks |
|
| 101 | Root access keys | AWS recommends that you delete your root access keys because you can’t restrict permissions for the root user credentials.
|
| 102 | WAF |
|
| 103 | Organization |
|
| 104 | Assurance Programs |
|
| 105 | Auditing and Compliance |
|
| 106 | Vulnerability and Penetration Testing |
AWS customers are welcome to carry out security assessments and penetration tests against their AWS infrastructure without prior approval for 8 services:
|
| 107 | Cost Management Prediction Tool |
|
| 108 | Cost Management Incurred Tools |
|
| 109 | Kinesis |
|
| 110 | Elastic IP address |
|
| 111 |
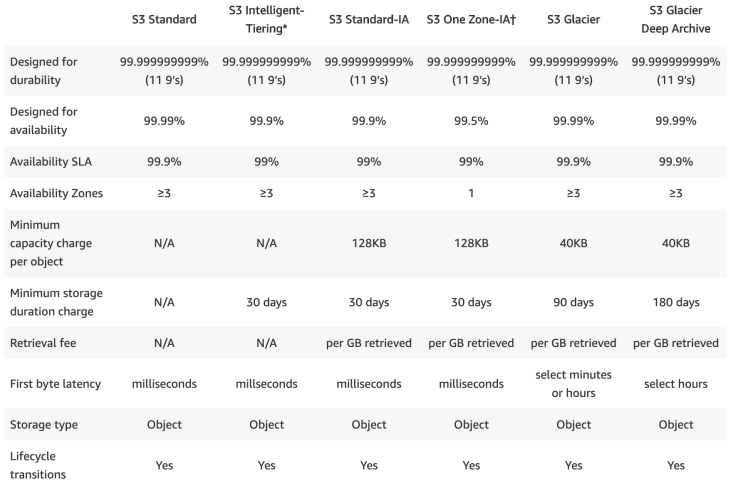
S3
- S3 names must be unique across all AWS accounts world wide, and must follow specific naming rules.
- Durability is a fault-tolerant.
- Backed with the Amazon S3 Service Level Agreement for availability.
- The only way to set an object’s storage class to Glacier is through CLI or SDK, no from AWS mgmt console.
- Storage cost and Request pricing are wrt Regions.
- S3 Lifecycle Management for automatic migration of objects to other S3 classes.
- Storage Classes can be configured at the object level and a single bucket can contain objects stored in S3 Standard, S3 Intelligent-Tiering, S3 Standard-IA, and S3 One Zone-IA.
- Cost factor:
- # of requests
- Data transfer
- S3 security features
- Permissions
- Versioning
- Zone Replication
- Backup
- Encryption – client (at transit) + server side (at rest)
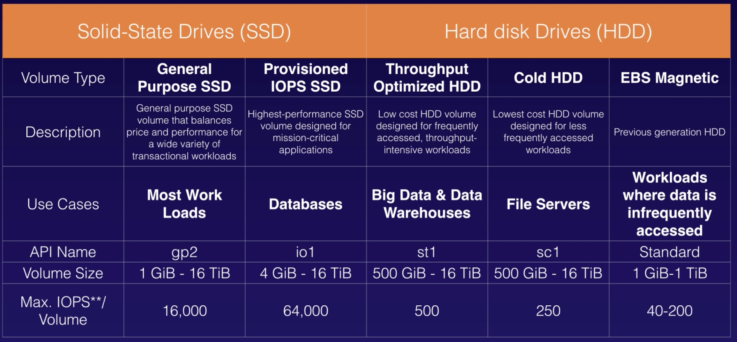
| Class | Explanation | Cost | Usage | |
| Standard | S3 Standard | GP-Storage of frequently accessed data | Highest | Cloud applications, dynamic websites, content distribution, mobile and gaming applications, and big data analytics. |
| Unknown & Changing Access | S3 Intelligent-Tiering | 2 Access Tiers:
|
Small monthly monitoring and auto-tiering fee | Unpredictable access pattern data |
| S3 Standard-IA | Long-lived, but less FA data, but requires rapid access when needed | Low per GB storage price and per GB retrieval fee | Backups, data store for disaster recovery files | |
| S3 One Zone-IA | 20% less than S3 Standard-IA. | Storing secondary backup copies of on-premises data or easily re-creatable data | ||
| Archive | S3 Glacier | Long-term archive and digital preservation.
3 retrieval options (few mins to hrs)
|
Cheaper than on-premises solutions | |
| S3 Glacier Deep Archive | Long-term archive and digital preservation.
Data accessed once or twice in a year. Alternative to magnetic tape systems. Restored within 12 hours. |
Lowest | Highly-regulated industries, such as the Financial Services, Healthcare, and Public Sectors — that retain data sets for 7-10 years or longer to meet regulatory compliance requirements. |
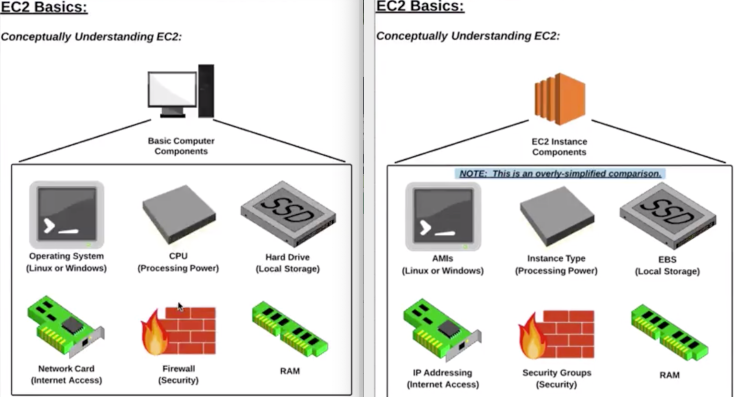
EC2
Instance Types Components
- Family: General purpose, Compute, Memory and Storage optimized, Accelerated computing.
- Type: Subcategory of family. m4.large | m4.xlarge | t3a.nano
- vCPUs: # of virtual CPU.
- Memory (GiB): RAM size.
- Instance Storage: Local HDD (EBS)
- EBS/ Network optimized features
- Hardware Specifications
- Nitro-based Instances: A collection of AWS-built hardware and software components that enable high performance, availability, and security.
- Nitro Components:
- Nitro hypervisor – A lightweight hypervisor that manages memory and CPU allocation and delivers performance that is indistinguishable from bare metal for most workloads.
- Nitro card
-
Local NVMe storage volumes
- Networking hardware support
- Management
- Monitoring
- Security
-
- Nitro security chip, integrated into the motherboard
- Nitro Components:
- Instance Limits: There is a limit on the total number of instances (20) that you can launch in a region, and there are additional limits on some instance types.
- Pricing:
- Buying option (On-demand, Reserved, Spot, Dedicated)
- AMI
- Instance type
- Region
- Data transfer in/out
- Storage capacity.
RDS
AWS manages:
- Server maintenance
- OS install / patches
- DB s/w install/ patches
- DB backup
- High availability and scaling
- Read replicas
Pricing
- Pricing depends on engine, On-Demand or Reserved Instances EC2 instances, storage, backtrack and data transfer IO you select.
- RDS provides a selection of instance types optimized to fit different relational database use cases.
- RDS is free to try. Pay only for what you use. There is no minimum fee. You can pay for RDS using.
DynamoDB
Pricing
- Pricing for on-demand capacity mode: pay per request.
-
Pricing for provisioned capacity mode: pay per prov capacity (1000 Rs, 100Ws)
SNS
- Pricing depends on Publishes, Notification deliveries and Data transfer
Cloudwatch
AWS List
https://www.parkmycloud.com/aws-services-list/
AWS Visual Diagram
https://www.lucidchart.com/documents/view/703f6119-4838-4bbb-bc7e-be2fb75e89e5/eNbqbEM6f5NI

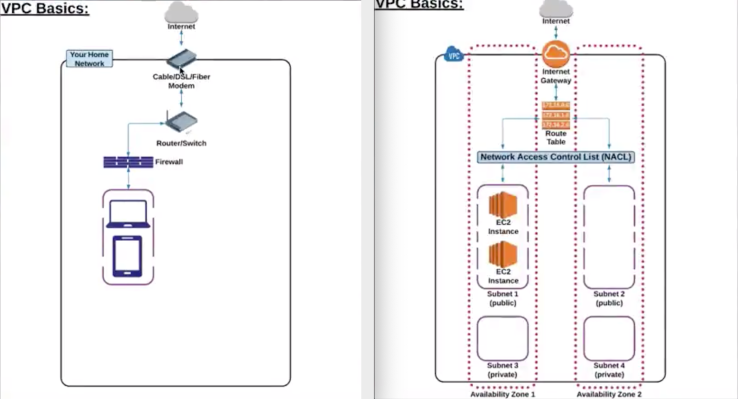
VPC
EC2
Route 53
ELB
Elastic Beanstalk
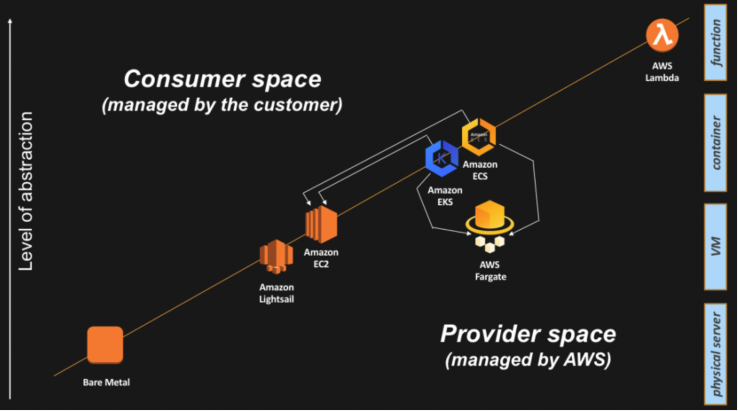
Control and Data Plane
Shared Responsibility Model

Other Services
| Analytics | |
| Athena | S3 SQL |
| CLoudSearch | Search in website and Apps |
| Kafka | to build real time streaming application, pubsub model |
| QuickSight | Business Analytics services, cost management |
| Data Pipeline | Move data between AWS resources |
| Glue | ETL tool for data in AWS |
| Application Integration | |
| Step Function | Visual workflow/state diagram of distributed application |
| Eventbridge | serverless service bus that connect outside SaaS and AWS |
| MQ | Managed Message Broker, active MQ |
| AppSync | Sync distributed data across all platforms [GraphQL] |
| AR & VE | |
| Sumerian | AR, VR, and 3D experience |
| Cost Management | |
| Cost Explorer | Analyze AWS cost and usage |
| Budgets | Set custom cost and usage budget, alert when exceed threshold |
| Reserve Instance Reporting | Reporting tool for reserved resources (EC2, RDS, ESS, ElasticCache, Redshift) |
| Blockchain | |
| Managed Blockchain | Create and manage blockchain |
| QLDB | Managed Ledger DB |
| Business Application | |
| Alexa for Business | For employees(day to day work) |
| Chime | meeting, video and chat (zoom, slack) |
| WorkDocs | online aws docs (like google docs) |
| WorkMail | Like outlook |
| Compute | https://aws.amazon.com/blogs/architecture/compute-abstractions-on-aws-a-visual-story/ |
| Elastic container Registry | Docker registry |
| EKS (Elastic Kubernetes Services) | run managed Kubernetes (like autoscaling of EC2, it is for containers) |
| Fargate | Compute engine for ECS and EKS |
| Lightsail | POD. Virtual Private Server. All in one VM for application development ( has server, db, lb) |
| Outposts | Onpremise DC AWS, two variant: 1. VMWare cloud on AWS Outposts 2. AWS native variant of AWS Outposts |
| Serverless Application Repository | github for serverless computing |
| VMWare Cloud | Control plane, converting Vsphere based env to EC2 in cloud |
| Control Plane | responsible for exposing the API and interfaces to define, deploy, and lifecycle containers |
| Data Plane | responsible for providing capacity (as in CPU/Memory/Network/Storage) so that those containers can actually run and connect to a network |
| Customer Engagement | |
| AWS Connect | Support customer service |
| Pinpoint | CRM tools, customer engagement platform |
| Management and Goverance | |
| Control Tower | manage multi aws account for compliance |
| Console mobile Application | aws mgmt console for mobile |
| License manager | Manage license |
| Managed Services | automates common activities, such as change requests, monitoring, patch management, security, and backup services, and provides full-lifecycle services to provision, run, and support your infrastructure. |
| OpsWork | configuration management service: Chef and Puppet are automation platforms that allow you to use code to automate the configurations of your servers. OpsWorks lets you use Chef and Puppet to automate how servers are configured, deployed, and managed across your Amazon EC2 instances or on-premises compute environments. |
| System Manager | Operation insights dashboard |
| Well Architected tool | input requirements -> get architecture design |
| Networking: | |
| Private Link | Private connection between resources eliminating the internet but uses amazon network |
| Direct connect | Connection between onpremise and aws |
| App Mesh | monitor and control microservices running on AWS. App Mesh standardizes how your microservices communicate, giving you end-to-end visibility and helping to ensure high-availability for your applications. |
| Cloud Map | service discovery for cloud resources |
| Global Accelerator | it is AWS GLOBAL network (private aws internet) |
| Transfer accelerator | data arrives at an edge location, data is routed to Amazon S3 over an optimized network path. |
| Transit Gateway | Inter VPC connection/on-premise, traffic routed by central transit gateway |
| Security | |
| artifacts | access reports and details of security controls |
| Certificate Manager | SSL/TLS cerficate service for internal connected resourses |
| CloudHSM | Hardware security model |
| Resource Access manager | Resource share |
| Secret manager | Key vault |
| security hub | hub for security alerts (guardduty, macie, inspector will sent event alert to hub) |
| Storage | |
| Amazon FSx for Lusture | mount file system interface for high performance to process S3 data |
| Windows FSx for windows file server | NTFS |
| AWS Backup | backup everything centrally from aws resources |
| Snowball | 50 TB to 80 TB, no compute |
| Snowball edge | snowball with compute, 100TB |
| Snowball mobile | 100 PB, no compute |
| storage gateway | convert tape, file and volume storage from onpremise to S3 classes and EBS |
| Migration | |
| AWS migration hub | tracking the progress of migration |
| Application discovery service | tool to discover/analyze on-premise resources and plan aws migration |
| DataSync | on premise SAN storage to AWS (S3 or EBS) |
| Server Migration | automatically replicate live server volumes to AWS and create Amazon Machine Images (AMI) as needed. |
| Transfer for SFTP | transfer file using SFTP to S3 |
| CloudEndure Migration | Complete cloud migration (OS+server+db) |
| Desktop | |
| WorkSpaces | Virtual Desktop Infrastructure (VDI) |
| AppStream 2.0 | application streaming service |
| ML | |
| Comprehend | relationships in text |
| Lex | voice and text |
| polly | text to voice |
| Rekognition | image analyzer |
| Translate | tranlate langs |
| Transcribe | closed-caption |
| Elastic Inference | running deep learning inference |
| Forecast | Forecast |
| Textract | extracts text and data from scanned documents |
| Personalize | individualized recommendations |
| Mobile | |
| Amplify | mobile applications |
| AppSync | serverless back-end for mobile, web, and enterprise applications. |