Integrity
- Integrity is used to make sure that nobody in between the two partners has changed the message.
- Integrity means that on the route from Alice to Bob, the message has not changed in between.
- Hashing technique can be used for this purpose to calculate the hash of message and send along with the original message.
- Hashing can be achieved through Message Digest (just plain hash) or HMAC (using symmetric key) or Digital Signature (using asymmetric key) of message.
Confidentiality
- Confidentiality is used to make sure that nobody in between the two partners are able to read the message that has been sent.
- Encryption technique can be used for this purpose to encrypt the message with a key (secret or private key).
Authenticity
- Authenticity would mean that messages received by Alice are actually sent by Bob.
- Authenticity is used to make sure that one partner really communicating with the other partner you want to communicate.
- Pre-shared key technique can be used for this purpose that are configured between partners.
Non-repudiation
- If the recipient passes the message and the proof to a third party and the third party can be confident that the message originated from the sender.
- More precisely, Non-repudiation is the assurance that someone cannot deny something. i.e., once sender sends the message to the receiver, the sender can’t say that I didn’t send this message to the receiver.
- Non-repudiation is about Alice showing to Bob a proof that some data really comes from Alice, such that not only Bob is convinced, but Bob also gets the assurance that he could show the same proof to Charlie, and Charlie would be convinced, too, even if Charlie does not trust Bob.
Difference b/w Integrity, Authenticity & Authentication and Non-repudiation?
- Authentication is NOT Authenticity.
- Authentication is establishing that Alice talking to Bob, while authenticity is establishing that the message actually came from Bob.
- Authenticity would imply integrity, but integrity wouldn’t imply authenticity.
- For example, the message may retain its integrity, but it could have been sent by Charlie instead of Bob to Alice.
- If Symmetric Key (pre-shared key) used then you’ll achieve Authenticity.
- Non-repudiation would imply authenticity, but authenticity wouldn’t imply non-repudiation
- For example, the message may show who sends it (authenticity), but the sender may deny it unless Public Key crypto used.
- If Asymmetric Key used then you’ll achieve Non-repudiation.
- Trust hierarchy of is like this (highest to lowest):
- Non-repudiation (provides via Digital Signature – Asymmetric Key)
- Authenticity (provides via MAC – Symmetric Key)
- Integrity (provides via MD or MAC – Symmetric Key)
Does SSL/TLS provide non-repudiation service?
- There is no non-repudiation for regular TLS packets.
- When Alice tells Bob “Let’s kill the president!” and Bob goes to tell the police, then Alice can always say: “I never said that.”
- So Alice just repudiated the previous statement.
- Regular TLS there is no way for Bob to prove by himself that Alice has in fact repudiated her earlier statement.
- So no, regular TLS does NOT provide non-repudiation.
- TLS packets are MACed and not Digital Signatured
- Since Alice and Bob both know the secret-MAC-key either one of them can generate MAC-values for whatever message they like.
- A MACed message says NOTHING about authorship of either Alice or Bob.
- So if Bob goes and tells Charlie: Here’s something evil Alice said!, then Alice can rightfully say: You could have written that yourself!.
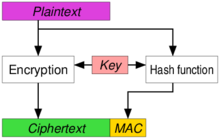
Authenticated Encryption
- Authenticated Encryption (AE) and authenticated encryption with associated data (AEAD) are forms of encryption which simultaneously assure the confidentiality and authenticity of data.
- AE mode implementation would provide the following functions:
- Encryption
- Input:
- Plaintext
- Key
- Header (optional) in plaintext that will not be encrypted, but will be covered by authenticity protection.
- Output:
- Ciphertext
- Authentication Tag (MAC).
- Input:
- Decryption
- Input:
- Ciphertext
- Key,
- Authentication Tag (MAC)
- Header (optional)
- Output:
- Plaintext, or an Error if the MAC does not match the supplied ciphertext.
- Input:
- The header part is intended to provide authenticity and integrity protection for networking or storage metadata for which confidentiality is unnecessary, but authenticity is desired.
- Encryption
- Approaches to AE
- Encrypt-then-MAC (EtM)
- Encrypt-and-MAC (E&M)
- MAC-then-Encrypt (MtE)
- Encrypt-then-MAC (EtM)
Credits: https://crypto.stackexchange.com.